It gives you a clearer idea of the true meaning of owning, sending, and exploring the digital currency.
I will begin with a brief and advanced overview of the meaning of the composition.
Bettokin – in essence – is a digital file that contains accounts and money and resembles a book of accounts.
Each computer in the network maintains a copy of this file.
These numbers do not represent anything in the real world.
These numbers have value only because people
Are willing to trade services and goods for a higher number in their accounts.
And believe that others will do ideals,
These numbers have value only because we believe it.
This is no different from any other paper currency.
If you want to send money you have to broadcast your desire in the network that you want to decrease the number in your account
The figure rises in the receiver’s account.
The contract (or computers) in the netting network executes this transaction in its version of the ledger
This transaction is then sent to another contract.
In addition to the above, some basic security measures based on mathematics, and that’s all!
It is a system that allows a group of computers to maintain a book of accounts.
This may look similar to the way the bank keeps its ledger.
But having a book of accounts with a group of people rather than one institution leads to a host of important features.
For example, you only know about your deals when dealing with a bank.
As for the Bettkin, everyone knows about all the deals that happen.
You can trust your bank or at least you can prosecute it if it goes wrong.
In Bettkwin you deal with unknown strangers so you should not trust anyone!
The system is designed so that you do not need any trust!
Where mathematical equations protect everything in the system.
The rest of the video will explain in detail how the developers can
To allow a group of outsiders to organize financial transactions for each other.
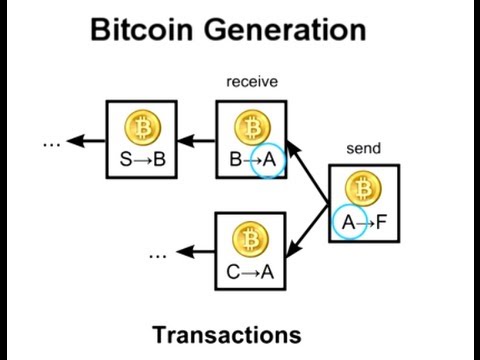
Simply put, if Alice wanted to send money to Bob,
You send a message containing the accounts and the amount of money you want to send.
“Send 5 pieces of Bettkwin from Alice to Bob”.
Each node that receives the message then copies it from the account book
And then resend this message to others.
But how can the contract know that this request is not forged?
That is, the account holder sent the message.
Rules of configuration require some kind of passwords that allow money to be sent
This password is called a digital signature.
This is similar to a written signature that proves that the application is not forged
But does so by a mathematical algorithm that prevents copying or fraud in the e-Kingdom.
This is different from using a static password,
Each transaction needs a different digital signature.
Remember that you’re dealing with strangers so do not show them any passwords they copy or use elsewhere.
The digital signature works by using two different but related keys.
The first is a secret key to create the digital signature
The other is a public key that can be used to validate the signature.
Consider that the secret key is the real password
A digital signature is an intermediary that confirms that you have the password without having to show it.
The public key is used as the address of the addressee in the configuration.
When you send money to someone you send money to their public key.
To send money, you have to prove that you are the real owner of the public key from which the funds were withdrawn.
To do this, you must create a digital signature using the message containing the transaction and the secret key.
The other nodes in the network
Use this signature in another function to verify that it matches your public key.
The underlying mathematics behind the digital signature allows confirmation that the sender has the secret key without having to see it.
Because digital signature generation depends on the message,
The digital signature will be unique in every deal.
And therefore can not be reused for another deal.
This reliance on the message means that no one will be able to modify the message while it is being sent to the network.
Because any modification in the message will make the signature false.
The mathematics behind this is very complex,
I will not try to explain it in detail now
But I’ll give you some words that you can start looking for:
ECDSA and mathematical trap door.
I will explain more at the end of the video.
We know so far that the digital signature is used to prove that the transaction is not forged,
But I have oversimplified the mechanism by which the contract tracks changes in account balances.
In fact, the contract does not store account balances at all.
But if you do not store the amount of money each person owns,
How do you know they have enough money to send to others?
Rather than storing credits.
Prove ownership of enough money by linking them to previous deals.
I will explain how this happens.
To send Alice 5 pieces to Bob,
They must refer to other transactions in which they received five or more pieces.
These other transactions are called “income”.
The other contract checks these receipts to make sure Alice has received the money
And that the sum received is greater than or equal to five pieces.
Let’s look at a real deal to see how this happens.
This transaction refers to six income totaling 139.6 pieces.
Note that the output has two lines.
The first is to return the surplus money to the sender.
A rule states that all funds in an income must be used in the transaction.
If you want to send a sum of money that is not exactly equal to the amount of money in the income you referred to,
You should send any surplus money back to yourself.
By referring to the inputs, ownership of the protein is transferred in a similar way to the chain,
Where the legitimacy of a transaction depends on the legitimacy of previous transactions,
But how do you trust the legitimacy of these previous deals?
Answer: You can not!
You have to check the legitimacy of their income as well.
In fact, after the inauguration of the First Time Portfolio Program,
The program downloads every transaction made since the start of the installation
And then verify their legitimacy one by one until you verify the legitimacy of the first deal was made.
Remember that you are dealing with strangers
So it is necessary to verify the legitimacy of each transaction yourself.
This science can take more than 24 hours
But you will not need it more than once.
And once a transaction is used once
This transaction is considered a waste and can not be used again.
And only one of them can use one of his earnings several times to refer to them in several deals.
Therefore, when verifying the legitimacy of transactions, the contract ensures that its income has not been disposed of before.
To be frank, and for every income
The contract is verified from all previous transactions to ensure that this income has not been disbursed before
This may seem a waste of time
Because there are more than 20 million deal now,
But it is quick to have an index of undisclosed transactions.
If the contract is replaced by a book of accounts,
It has to track a huge list of deals.
And the possession of the digital currency (composition)
Means that there are transactions that indicate your name in this list and have not yet been acted upon
(Ie, not referred to as income in other transactions).
And one of the important results of this property model
Know your balance of the digital currency
Needs to pass through every deal made
Then collect all your undisclosed income.
Add an important note:
That the system can support more complex deals than just sending money from person to person.
You may have noticed the incomprehensible line in the transaction exit we previously presented.
Since the output is like an issue that needs to be resolved instead of being a simple container on the addresses of the addressees.
Instead of sending money is like sending a message,
Sending money is like putting money in a safe
And lock it with the issue of mathematics must be solved until you open the safe,
Math is defined as a special programming language,
Although specifically designed to be solved by a single owner of the public key,
There are many other possible possibilities.
For example, we may need two out of three signatures to pass a deal based on a third party guarantee.
Another example is the first deal ever made, which contained an issue that anyone could solve.
Most wallets hide this layer of software
But you can program your own program even though this is risky.
More than 2,600 pieces have disappeared due to address errors in a range of deals.
And this emphasizes the important thing when dealing with Albtkwin,
Since you can not go to a bank or credit card company
Any errors by the user may result in permanent loss of digital parts,
This loss is not limited to your account
It is a loss of the entire economy.
If you lose your secret key
Any funds associated with the corresponding public key will disappear forever.
And as people will lose their keys often
For reasons such as hard disk failure and no backup,
It means that the mint currency will contract with time.
Before I talk about the latest technique that ensures the work of Bettkwin (exploration)
I would like to point out a couple of points about privacy when dealing with developers.
If you enter a configuration over a Tor network that hides your IP address,
You can use the configuration without showing anything other than your public key.
And to avoid someone tracking all your deals
(Remember, all transactions are stored on all computers!)
You can generate a new generic key for each incoming transaction.
However, these public keys can be inadvertently connected.
In the deal we presented earlier, six other deals were used as sources of money,
And that all these revenues have been received at different addresses
They are all associated with this transaction.
The sender has proved ownership of all these titles
Through the provision of the electronic signature required to unlock each of them.
The researchers used these links to study the behavior of the protein user.
You may think that generating a public key to receive money may ultimately lead to revealing your true identity,
But even this step is kept secret.
And can be done offline!
Where you simply press a dedicated button in the wallet program
The program generates a new generic and special key.
And since there are many possibilities for these titles,
There is no need to make sure there is no other person with the same address.
Compare this with the registry for an email service
Most of the names you might think are already used.
In fact, if you can guess someone else’s key you’ll own all his money!
This is the number of all possible possibilities for the initialization addresses.
These enormous numbers protect the system in many ways.
It is useful to try to imagine how big,
Some estimate the number of sand grains in the globe at 7.5 million trillion,
And now imagine that each grain of sand represents another land full of other sand,
However, the figure will remain much lower than the potential of the initialization addresses.
Let us summarize what we have learned about the security of fortification so far.
By verifying the validity of the electronic signature.
We can know that only the legitimate owner is able to send the transaction
And to verify that the sender has enough money to spend.
Check each income you refer to to make sure it is not expended
But there is still one loophole in the system
This makes “checking that transactions are not debited” unreliable.
This gap is related to the arrangement of this transaction.
Since transactions move from node to node across the network,
There is no guarantee that the order in which these deals were received is the same as the order in which they were created.
And do not trust the time recorded on the deal
Because the owner of the deal can easily lie about when the deal was created.
We therefore have no way of knowing whether a transaction was established before the other
This opens the door to fraud.
A wily user like Alice can send a deal to send his money to Bob,
Bob then waits until the goods are shipped to him,
He then sends another deal indicating the same income and returns the money to himself.
Because of the differences in the transmission speed of the message,
Some nodes in the network will receive the second message (in which funds have been transferred to themselves)
Before the letter where money is spent on Bob.
When the deal with Bob arrives, it will be considered illegal
Because it is trying to re-spend an income.
Bob loses both his merchandise and his money.
The result will be a dispute within the network whether Bob or Alice owns this money
Because there is no way to prove that a deal came first.
Thus, there must be a way for the entire network to agree on the order of occurrence of transactions,
It is complex in a decentralized system.
The solution in the system is a smart way to ensure the identification and protection of the order of transactions
Through a kind of sports race.
The Bettkin system arranges transactions by placing them in groups called blocks,
And then link these blocks with each other in the so-called series of blocks.
Note that it is different from the series of deals we talked about previously.
Where a series of blocks is used to arrange transactions,
While serving a series of transactions to track ownership of funds.
Each cluster is referred to as the previous cluster,
This makes one block precede the other chronologically.
Where you can follow these signals towards the past until you reach the first block of transactions that have occurred.
We see that transactions in a single block occurred at the same time.
Transactions that have not yet been included in a block are called unrated or unrecorded transactions.
Any node can combine several undocumented transactions into a cluster
This block then suggests the rest of the nodes in the grid to be the new cluster in the string.
Because several people can create several blocks at the same time,
There are several possible options as a new block.
How can the network decide which clusters are the next in the series?
We can not rely on the order of the receipt of blocks,
As we explained earlier about deals,
These blocks can arrive in different order in different nodes in the grid.
Part of the solution is that each block must contain a solution to a distinct mathematical issue.
Where computers use text in the cluster as well as random numbers
To create so-called “encrypted fragmentation”
Until you find a product that is less than a specific value.
The Hash Affiliate generates a short result from any text, whatever its length,
In our case, the result is a 32-byte number.
Here are some examples of the fragment used in the SHA256 system
Notice how the output changes frequently after adding one point at the end of the third example.
No one can ever predict the outcome
Thus, the only way to find a particular product is to do random guesswork.
This is similar to trying to guess the password to lock.
You may be lucky in your first attempt,
But you need a few guesses.
In fact, it may take a few years for a normal computer to find a true guess that resolves the mass.
All computers on the Netcom network are guessing numbers,
It takes ten minutes to find a compromise.
The first to find a solution to the question of mathematics is the mass
The range of transactions contained in it becomes a new block in the chain.
The random mathematical issue leads to different times when people find a solution to it
Which reduces the likelihood that two will find a solution to the issue at the same time.
But several blocks may solve at the same time sometimes
Leading to several possible branches.
In this case you have to build on the first block you receive.
Others may receive blocks in different order
And each will build on the first block received.
This node is resolved when the next block person resolves.
The rule always adopts the longest chain available.
Math makes it possible to dissolve blocks at the same time.
The likelihood of this happening several times in a row is weaker.
The result is that the series of blocks stabilizes quickly,
This means that everyone agreed to order the added blocks to the end of the string.
The ambiguity at the end of the chain has a significant impact on transaction security.
For example, if your position falls on the short branch in the string you will lose its place in the series of blocks.
This means that it will revert to the undocumented transactions,
It may later become a component of a new mass.
Unfortunately, the possibility of a deal losing its place in the chain opens the door to a double spending attack
Which was the first reason that led us to invent the order system.
Let’s see how the multiplier spending attack works in the system we’ve described so far.
A fraudster (Alice) sends money to Bob.
Bob is waiting for the deal to be documented in a series of blocks and then shipping the goods.
Now, because the contract always chooses the longest chain,
If Alice can generate a longer chain in which the deal with Bob is replaced by another deal with another person,
His money will be removed from the chain.
Bob’s deal will initially return to undocumented transactions.
But since Alice replaced it with another deal where the same income was spent,
The deal will be considered a bad deal, because it depends on an already spent income.
How does the ranking system prevent Alice from cheating Bob?
You might think Alice can pre-calculate a series of blocks to suggest on the web in time,
But the mathematical issue in each block prevents such a.
We need to know more deeply about the encoded parser we talked about in advance to fully understand the reason.
As I mentioned earlier,
The cluster solution depends on trying to make the encrypted hash output of the block less than a certain value.
You do this by experimenting with different random numbers at the end of the block.
The output after finding it becomes a distinguishing mark of this block (fingerprint).
And changing one character in the cluster will make the retail product completely different,
As we saw earlier when we added a point.
Use the ticker, or footprint, to refer to the previous block.
Thus, a block can not be replaced in the center of the string because the new cluster mass will vary,
The signal in the next block will no longer be indicated.
And the obvious result, but more importantly, no one can solve a block before the mass that precedes it.
And the reference to the previous cluster is part of the body of the cluster that enters the hash,
Any change in it will need to be resolved again.
And back to Alice,
Our science has not been able to calculate a branch in advance.
You can start to dissolve a block only if the block you want to build on is resolved, and the tick value is known.
And therefore they are in a race with the rest of the network until Bob ships the goods,
This is the time Alice wishes to introduce her longer branch.
And ask the last question
Is it possible that Alice can precede all if she has a supernatural computer,
Or perhaps a room filled with computers.
Even if you own thousands of computers will not be able to win the race and solve the block,
Because they do not race individual computers,
But raced the entire network.
This is more like a lottery game.
It can use thousands of computers,
Or to buy thousands of lottery tickets,
But even if you do, someone else’s chances of winning are high.
It must have more than half the computational power of the entire network
To be her chance to dissolve the block before another person 50%.
And it has to have much more to be solved by several sequential blocks before the rest is larger.
Deals are protected in a series of blocks by a sports race,
This race puts the striker against the rest of the entire network.
The creation of new blocks above the old results in the older blocks in the string being more secure.
The attacker must precede the network for longer
The double spending attack succeeds in replacing an old block with another.
The system is subject to a double-spending attack near the end of the series,
For this reason it is advisable to wait until a few new blocks are added
Before the receipt of funds is considered final.
A final note about the series of blocks before I begin to explain the last issue of the system of protein.
What is surprising is that all of the above and his explanation does not require any confidence.
If you receive information from strangers on the network,
You can make sure that the cluster solutions are correct.
Because math is difficult, you’re sure there’s no attacker capable of making it.
The existence of solutions proves to be due to the computational ability of the entire network.
After we talked about the mechanism of sending money through digital signature and transaction chains,
And how to protect the order of these deals in the series of blocks,
Let’s talk about the last topic: Where does the coin come from?
You have to point out an old deal where you are the receiver before you can send the money,
But how do these funds enter the property chain at first?
The way in which the pieces are generated and distributed randomly,
Is to give an award to anyone who finds a solution to a block.
This is called the solution of the blocks “exploration”,
Although the primary objective is to document transactions and protect the chain of blocks.
The prize is cut every four years in half and in the end no new pieces will be created,
There will be about 21 million pieces in the end.
Remember that you can send the equivalent part of the 100 million part of the piece,
Therefore, the limited number of pieces will not affect our ability to use them.
When the awards stop,
What incentives will pay prospectors to handle deals?
Prospectors can receive, with their prizes, any transaction fees
Which may be optionally available within such transactions.
Prospectors now add deals without fees to the blocks
Because their main goal is the award after the dissolution of the block,
In the future, deals will mostly be handled according to the fees attached,
Non-fee transactions will often be ignored.
Therefore, sending the money in the content will not be free,
But we hope it is cheaper than the fees charged on credit cards.
As I mentioned earlier, an average computer will take several years to solve a block,
So one person’s chance of solving any block before the rest of the network (which usually takes ten minutes) is very low.
In order to obtain stable financial income,
Many people join groups called mines
Which cooperate to dissolve a block and then distribute resources based on the amount of participation.
This is similar to the cooperative lottery groups,
Except that some of these mines are very large, making up more than 20% of computers on the network.
The presence of these large mines has an important impact on safety.
As mentioned earlier, one attacker can not solve a series of serial blocks before the rest of the grid,
But this becomes possible, and the more likely it is, the more powerful the attacker will be compared to the rest of the network.
One of the mines, the Union of Pettokin, has already managed to solve six clusters,
The number of its employees has been voluntarily determined to prevent the breakdown of confidence in the network.
Even with high computing power,
The earlier the deal is in the series, the more difficult it will be to change.
It is currently recommended to wait for one block, or obtain one document, before transmission is considered final.
For great deals, wait at least six blocks.
And with the ability of the Syndicate to solve six sequential blocks you might have to wait longer.
The blocks are designed to require ten minutes to be solved,
So you have to wait a full hour until you solve 6 new blocks.
If you compare them with the few seconds it takes to send a credit card transaction,
You’ll be waiting all this time to document a deal is annoying,
But remember that credit card users can claim to steal their card after several months
And to return their money from traders,
Thus, the fabrication is much faster than the trader’s.
The choice of ten minutes was random,
But very short time will lead to instability,
The long time will delay the documentation of the transactions.
With more computers joining the network,
With the design of computer equipment for exploration,
The time needed to solve a block will decrease.
To compensate for this,
All programs begin to evaluate the difficulty of mathematics issues every two weeks
So that the solution takes ten minutes.
On the other hand, another digital currency called Letquin has been able to operate at a time of 2.5 minutes per block.
In summary, decomposition is a digital coin protected by mathematics
And saved by users on the network.
The digital signature gives individuals the right to make deals,
Ownership is transferred through a series of transactions,
And saves the sequence of transactions occurring in order in the series of blocks.
And in order to solve the issue of mathematics for each block,
We put the attackers in a competition they can not win against the rest of the network.
The future will be a lot of creative ideas,
Such as preventing government intervention and secrecy and reducing remittances.
There are many challenges, such as the difficulty of exchange of currency with other currencies,
And was classified as a refuge for illegal acts and evasion of taxes,
So governments may try to prevent it.
In addition, the math race that protects the series of blocks consumes a large amount of electricity.
If you want to read a written copy of the video
You can check my blog,
imponderablethings.com
The code contains further explanations of the mathematics behind the encrypted digital signature and fragmentation that support the system.
”
Be First to Comment